By Jeff Domansky, May 5, 2021
Three-quarters of financial institutions (74%) saw a significant spike in Covid-related fraud and cybercrime in the past 12 months.

New research by BAE Systems Applied Intelligence shows a substantial jump in new pandemic-related threats, along with more significant security challenges caused in part by enforced work-from-home guidance, leaving open and insecure gaps in FI networks.
42% of banks and insurers revealed remote working has made them less secure. Just under half (44%) said that this has led to less visibility of potential holes in their network or infrastructure and a further 37% of FIs believe their customers are now at greater risk of cybercrime or fraud.

“We’re noticing a clear collaboration emerging between different groups of criminals across the wider landscape of serious and organized crime. Fraudsters and cyber criminals seek to exploit fear, uncertainty, and change, and the pandemic has offered them new opportunities to probe for weaknesses they can monetize and new ways to disguise their activity,” said Adrian Nish, Head of Cyber at BAE Systems Applied Intelligence (BAE).
Data shows cybercrime growth rampant
Financial losses were experienced by 56% of FIs with an average cost of $720,000 and rising over the past 12 months. Many incidents go unreported, not discovered for months or more, or opaquely hidden from public disclosure because of reputation damage or further financial risk.
BAE’s research indicates cybercrime is increasing across the board:
- +35% increase in botnet attacks
- +35% growth in ransomware
- +35% jump in phishing attacks
- +32% increase in mobile malware
- +30% Covid-related malware increase
- +29% growth in insider threats 29%.
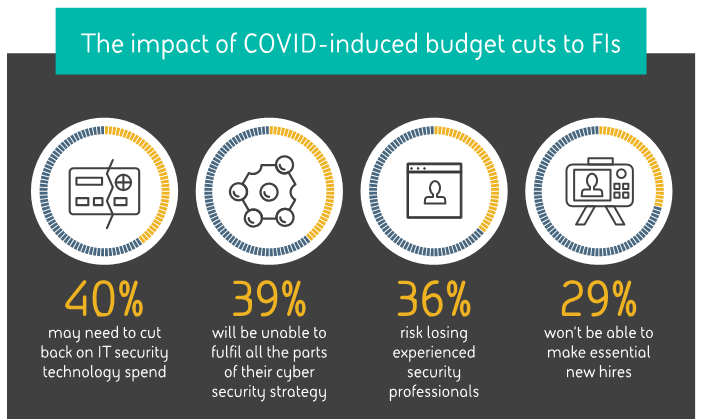
Part of the problem may be budget cuts that averaged 26% across the businesses surveyed in IT security, cybercrime, fraud, or risk departments. That’s almost the same amount that detected criminal activity had risen by (29%) since the start of the pandemic.
Work from home added to cybersecurity risk
Work-from-home and remote teams make monitoring and security even more difficult.
“The mass shift to remote working had a major impact on corporate cyber risk, making it harder for security teams to work effectively and expanding FIs’ cyber perimeter. Over half (51%) of businesses surveyed claimed they were forced to adapt their security strategies as a result of the shift to distributed working — taking an average of 18 weeks to do so,” the report notes.
The report also found a significant majority (14%) of businesses surveyed claimed the productivity of IT security teams declined when forced to work from home, creating opportunities for cybercriminals.
“Attackers are building increasingly advanced capabilities to target core banking systems and becoming more aggressive, harming victims’ ability to respond to attacks. Online criminals have reacted fast, adapting their approach to hunt out remote working security gaps and prey on the vulnerable,” Nish said.
Consumers hit by cybercrime too
BAE also examined the impact of Covid-related cybercrime on consumers and found 20% of FI customers were affected.
More than one-quarter (28%) of customers said they received an email hoax relating to COVID-19, with 22% targeted by text or SMS. Even when refunded, the average amount of money stolen by cybercriminals from customers was $1,174. For those who didn’t get refunds, the average money lost was a significant $743.
The jump in Covid-related cybercrime is partly due to more online shopping and new online shoppers less familiar with fraud prevention and protection of personal information. Nish noted 26% of customers said they purchased from a fraudulent site in the past 12 months and never received their products.
Even more shocking, cybercriminals victimized 38% of consumers with fraud or hoaxes in the past 12 months at least once, with 24% twice, and 15% hit three times.
First Horizon Bank breach loss nears $1 million
BAE and 84% of consumers were concerned about sharing their digital identity and personal information. They have good reasons for concern, as a recent Tennessee bank security breach illustrates.

In an April 28 filing by First Horizon Bank with the SEC, the company explained a severe security breach discovered two weeks earlier:
“Based on its ongoing investigation, the Company determined that an unauthorized party had obtained login credentials from an unknown source and attempted access to customer accounts. Using the credentials and exploiting a vulnerability in third-party security software, the unauthorized party gained unauthorized access to under 200 online customer bank accounts, had access to personal information in those accounts, and fraudulently obtained an aggregate of less than $1 million from some of those accounts.”
Cybersecurity experts point to the ongoing danger of cybercrime and the risk of third-party consultants and service providers, as well as new pandemic-related impacts.
“The First Horizon data breach is a stark reminder of the imminent dangers within the financial services industry due to the reliance on usernames and passwords. According to the Verizon Data Breach Investigations Report (DBIR), over 80% of data breaches occur due to credential theft resulting from passwords. Passwords are often weak or reused and can be easily stolen, guessed, or brute-forced,” said Rajiv Pimplaskar, CRO, Veridium.
Even two-factor authentication risky

Even two-factor authentication (2FA) with a one-time password (OTP), typically a six-digit PIN sent over SMS, is still susceptible to “man in the middle” attacks, Pimplaskar said. “A more secure approach leverages passwordless authentication methods such as “Phone as a Token” or FIDO2 security keys.”
“Establishing and verifying trusted digital identity across 3rd party B2B relationships is especially challenging during the COVID19 remote work climate. The Governance, Risk, and Compliance (GRC) profile of a contractor or 3rd party worker is very different when they are offshore and/or operating from an uncontrolled environment,” emphasized Pimplaskar.
“Many of such 3rd party relationships are transactional and have high flux, which further exacerbates the issue. Remote workforce identity verification, also sometimes referred to as Know Your Employee or KYE (similar to Know Your Customer or KYC on the customer side), along with strong modern/passwordless authentication methods, can help in reducing the attack surface and mitigate third party risk,” he added.
Pimplaskar said Gartner recommends enrolling an authentication factor as an “identity anchor” such as the employee’s smartphone or a FIDO security key during the identity verification process. This authentication factor can then be used on an ongoing basis to verify the individual and minimize the likelihood of credential compromise in the process.
Cybersecurity challenges are constantly changing and evolving. Financial institutions must continuously monitor, test, reevaluate and strengthen security among third-party service providers and consultants.
As the BAE data indicates, cybercriminals are anything if creative and constantly adapting to new threat opportunities and security vulnerabilities. This is no time for financial institutions to cut IT security budgets and reduce stringent standards for service providers and employees.
BAE Systems Applied Intelligence’s Covid Crime Index 2021 report can be downloaded free here.
Recent cybersecurity coverage:
12 billion records stolen last year; cybersecurity spend will grow +10%
The challenging state of small business cybersecurity


