There’s good news and bad news about identity theft in 2018 according to a new report from the Identity Theft Resource Center (ITRC).
The good news is the number of US data breaches decreased from a 2017 all-time high of 1,632 breaches by 23% to 1,244 breaches.

Unfortunately, the number of consumer records exposed containing sensitive personally identifiable information jumped 126% from 197,612,748 records exposed in 2017 to 446,515,334 records in 2018.
“The increased exposure of sensitive consumer data is serious,” said Eva Velasquez, president and CEO of the Identity Theft Resource Center. “Never has there been more information out there putting consumers in harm’s way. ITRC continues to help victims and consumers by providing guidance on the best ways to navigate the dangers of identity theft to which these exposures give rise.
Data breaches by sector
ITRC data provides a useful perspective on the industry sectors most impacted.

Businesses had the largest number of data breaches, but the lowest rate of exposure per breach. Healthcare had the second-highest number of data breaches, but they also suffered the highest rate of exposure breach.
Marriott International experienced the highest number of reported records exposed in 2018, impacting 383 million people worldwide.

“Unfortunately, for the bad guys these data breaches are gifts that keep on giving, long after the news headlines fade away. Millions of these stolen credentials find their way to the dark web, where they are acquired by other bad actors who then orchestrate automated bot attacks targeting other web sites where those credentials might give them fraudulent access to private accounts. Without proper security safeguards, those automated attacks can be quite successful because people tend to use the same login credentials on multiple sites,” said Franklyn Jones, CMO at Cequence.
Non-sensitive data theft is substantial problem
The theft of non-sensitive data is also a serious problem. ITRC reports an additional 1.68 billion records, primarily emails, were compromised in 2018.
While emails alone are not considered sensitive records theft, so many consumers incorporate email into online identification, usernames and password combinations, they are a growing risk and vulnerability.
“When it comes to cyber hygiene, email continues to be the Achilles Heel for the average consumer,” said CyberScout founder and chair, Adam Levin.

“In situations where a user has a weak password it is an “Aw-shucks” moment for the user, however the administrators of the system shoulder some of the blame as they allowed the users to be so careless. As an attacker, the more frequently you see an email address used as a primary logon method or recovery method, the more apparent it becomes whether that account is critical. If I have access to this email address, I can request password resets,” said Rod Simmons, VP of Product Strategy with cyber security firm STEALTHbits Technologies.
Simmons added a further concern: “Single Sign-on using technologies like Microsoft Account, Google Account, or Facebook are great for users, as it means there’s one less credential to manage poorly. The problem is once that credential is owned, not only can a bad actor assume your identity any place you have used, it they can use it in new places you are not aware of to assume your identity.”
Types of data theft wide ranging
The most common methods of data theft are wide ranging.
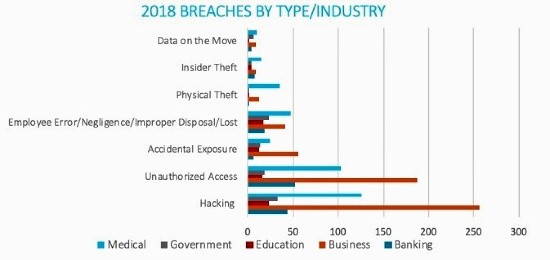
Hacking was the most common form of data breach in 2018, totaling 482 data breaches and exposing 16.7 million consumer records. Impacting the Medical, Government, Education and Business Sectors, hacking resulted in the third highest data exposure.
Unauthorized Access, the second most common form of data breach, totaling 377 data breaches, exposing 404.2 million records.
Accidental Exposure had the third highest number of breaches totaling 114 and ranked second in total number with 22.1 million records exposed.
Measurement is critical for security
Every business measures financials, sales, customer adoption, employee turnover and other key business metrics but cybersecurity management must also measurement.

“Without a truly metrics-driven approach when adopting best practices, especially cybersecurity frameworks such as the NIST Cybersecurity Framework, there is no tangible way to communicate program effectiveness. The only way we can continue to keep up- and more importantly get better at keeping up- with the “bad guys” is if we have an efficient cycle of best practice adoption, measurement, analysis, and remediation that is easily communicable and measurable like any other business function,” according to George Wrenn, CEO of CyberSaint Security.
Clearly the problem of stolen identity and personal records is growing and must be a top priority for business, government and any other online organizations. Hackers and criminals are increasingly sophisticated and move quickly to penetrate security weaknesses and capitalize on consumers with poor password practices.
You can read ITRC’s 2018 End-of-year Data Breach Report here.
Charts courtesy ITRC








LET’S CONNECT