By Jeff Domansky, May 28, 2021
Another week, another serious security lapse in the financial world.
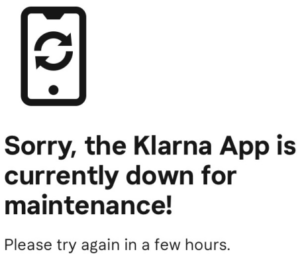
Klarna shut down its popular buy now, pay later payments app, used by more than 90 million shoppers worldwide. All due to what Klarna CEO Sebastian Siemiatkowski embarrassingly called “a self-inflicted incident, for 30 min, affecting the privacy of some of our users” on his Twitter account.
An app update introduced by the company at 10:45 am CET caused users logging in to the app to see random account information of other users. The error continued for 31 minutes before the company shut down user interfaces for the app.
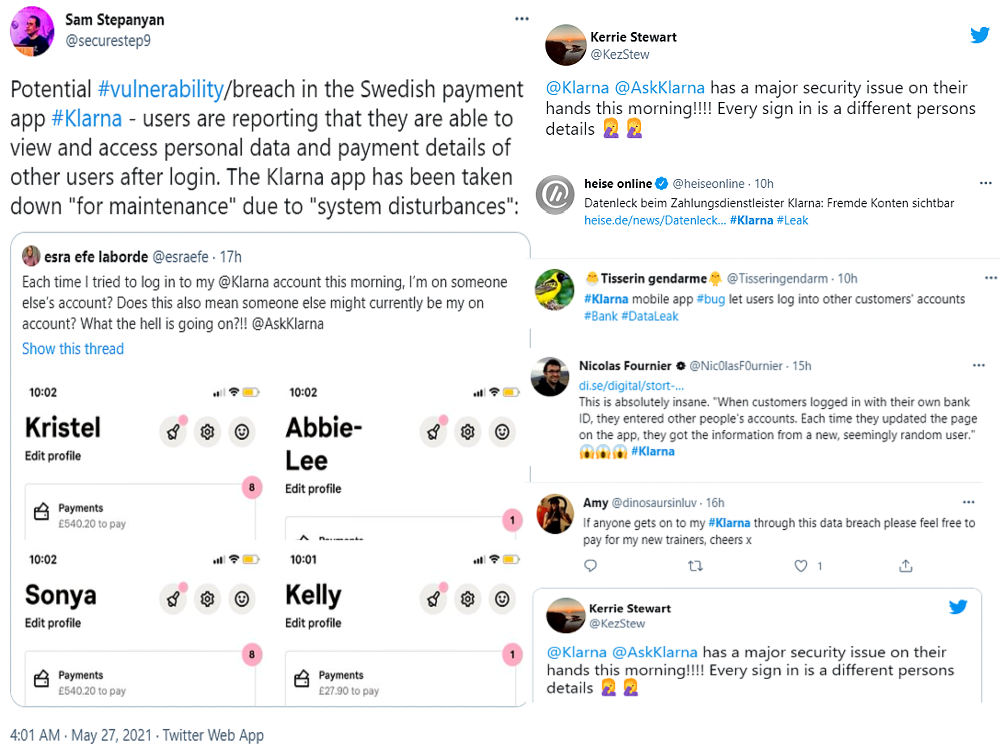
Users logged in and saw other user account info
Users reported logging in on the app only to see other user account information. Understandably, it set off a domino effect of concern across the internet and social media. Consumers bombarded Klarna looking for answers, worried about their own accounts, and expressing concern for their financial information and personal data.
Customers on Klarna’s website saw this message early in the day, and it remains live so far:
“We are currently experiencing system disturbances caused by a technical error. We apologize for any inconvenience this is causing. Whilst we are addressing the issue, customers are unable to log into the app.”
I guess the company didn’t appreciate the irony of the headlines on its homepage, which read:
“A payment experience that shoppers love.”
“No risks. Just benefits.”
Damage control underway
Six hours later, Siemiatkowski provided his only other comment and Twitter update:
“Incident update!We previously reported “up to 90 000,of our users could have been affected”. While obviously even a single exposure is unacceptable, continuous work on exact impact assessment has significantly reduced this so it most likely not more than 9500.More updates to come.”
Meanwhile, users were venting and unhappy with the security lapse. The company had some ‘splaining to do, but it’s been keeping its head low while trying to handle the problem.
My favorite tweet was from Twitter user Amy @dinosaursinluv who tweeted: “If anyone gets to my #Klarna through this data breach please feel free to pay for my new trainers. cheers x”.
Managing the problem and the message
On Twitter, the company account posted the following message as it tried to get its hands around the security problem:
“An update on the issues experienced this morning: The incident, caused by human error within Klarna, impacted 0.1% of our users – which is 0.1% too many. Our customers’ trust and safety remain our absolute top priority. You can read more here:”
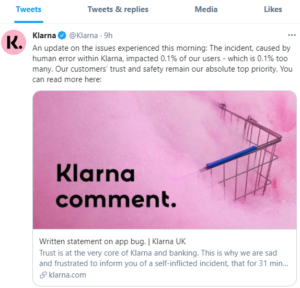
The Tweet took concerned users to a full blog statement issued by the CEO within hours of the initial incident.
In the blog post, Siemiatkowski attempted to explain the security lapse. Klarna concluded that “a human error caused the bug and it was not an external breach of our systems. Unfortunately, an inadequate risk assessment of a subsystem allowed for a handling error to be introduced into our live systems without proper quality assurances. As the root cause was quickly identified, we immediately took appropriate actions with dedicated teams working on this as a top priority.”
Meanwhile, back on Twitter, a company post from the day before was playfully asking for users to share comments which today rang ironic: “What’s your favourite Klarna purchase of all time? Wrong answers only…” Of course, it received many troll comments among the playful ones.
Klarna invoked its dormant @AskKlarna Twitter account to cross-post and help with answers for concerned customers.
Security experts quick to criticize
A roundup of security expert comments pointed to potential concerns.
“It’s hard to say what caused this issue without more data, but it has all the hallmarks of a BOLA (Broken Object Level Authorization) vulnerability. Our recent security research into mHeath apps and APIs surfaced similar issues. The key lesson is understanding the importance of ensuring that the user getting the data is really authorized to do so, and that this needs to be tracked all the way down the backend stack, not just on the perimeter,” observed David Steward, CEO of Approov.

Approov recently published a report where the company tested 30 mobile healthcare apps, and every one displayed API vulnerabilities that exposed personal healthcare data.
Research by Contrast Security in its 2021 State of Application Security in the Financial Services Report shows how big the challenge of app development and updates is:
“Despite enormous effort by the application security and development teams, applications still have a lot of vulnerabilities—both during development and in production. During development, 85% of respondents admit that the average application has 50 or more vulnerabilities – and 67% say that 20 or more of those vulnerabilities are serious.”
That’s an enormous security risk for payments and financial services apps for organizations big and small.
IT expert Marcus Murray says consumers are at growing risk as higher expectations are placed on banking apps. “This type of business has to deliver functions with higher intensity, week after week or every month. It creates security challenges. More and more competition between banks and credit companies increases the risk of security problems.”
“Every time a developer develops a new function, you can make a mistake, it can lead to security problems. Unfortunately, I am therefore convinced that we will see more and even more serious incidents like this in the future,” Murray added.
Incident resolved, but trust now a concern
Late in the day, Klarna offered an update to the CEO blog post, saying:
“Update: The incident is resolved.
At 11:04 am CET this morning we discovered that an update introduced 15 min earlier had led to an error affecting our app users. Our payment services, the Klarna Card, the merchant checkouts and the merchant’s user interfaces, were completely unaffected by this. At 11.20.42 am CET the error was deemed to be contained and fixed.”

While the developers and software engineers may feel comfortable resolving the incident, the bigger issues for Klarna now arise. The app developer team blew it. Fortunately, the number of consumers impacted appears small. So far, Klarna’s done a limited but reasonably transparent job of communicating about the issue.
In the meantime, I hope they take down the funeral-like floral arrangement photo on the blog post – it feels inappropriate. Same with the upside-down ice cream cone on their Pinterest account. Marketing and security issues rarely play nicely together. The company can come off looking remarkably tone-deaf unless they decide to go full-scale Monty Python or John Oliver-style on the issue. Maybe that might work in Sweden?
It’s another wake-up call for financial companies to be more diligent in their application development, implementation, and security management. Consumers and other stakeholders will be watching carefully to see how Klarna responds going forward.
Payment systems are built on trust. When that trust in data and payment security is lost, it takes enormous effort to restore it. The reputation damage can linger as questions start to come from regulators in the 17 countries where the company operates.

