New research from cybersecurity firm Proofpoint shows that imposter email and email phishing attacks on global financial services companies grew 60% over last year.
The FBI estimates that business email compromise (BEC) has cost organizations around the globe a potential $12.5 billion since the end of 2013.

Proofpoint’s analysis of more than 160 billion emails and 100 attacks on financial services company during the past two years showed 56% saw more than 5 employees targeted by impostor attacks in Q4 2018. Just 17% of targeted financial services organizations had only one person targeted in the same quarter.
Identity Deception Tactics
It’s not just that hacker technology is getting better. Fraudsters are getting more sophisticated in their attacks on people and seeing results from deceptive email tactics such as domain spoofing, display name spoofing, and lookalike domains.
“While email fraud is not unique to financial services organizations, this industry’s employees hold the keys to one of the most potentially lucrative paydays for cybercriminals. One wrong click can expose an entire brand and its customers to substantial risk and even bigger losses,” said Ryan Kalember, executive vice president of Cybersecurity Strategy for Proofpoint.

Email fraud is a broad category that includes business email compromise (BEC), a form of wire fraud, and other threats in which the attacker uses some form of identity deception to manipulate an individual. These attacks are socially engineered to target specific people within financial services organizations who can execute requests on the attacker’s behalf.
Most popular email attacks by category
Wire transfer scams are a big part of email fraud in the financial services industry according to the report:
“The top subject categories used to target financial services firms have included “payment,” “request” and “urgent.” Payment-related subject lines such as “payment status,” “payment request” and “swift transfer” were twice as common among financial services firms. They accounted for 10% of total messages vs. just 5% across all industries.”
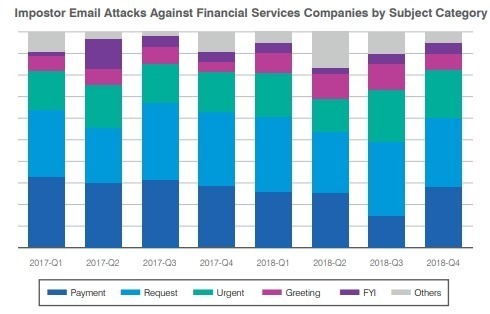
The report also identified scams shipment-related subject categories such as “UPS shipment notification” and “your tracking notification.” These were far more common in financial services organizations, representing 8% of imposter attacks, compared to 1% across all industries. Messages that included “account change request” in the subject made up 7% of attacks targeting financial services companies vs. just 2% overall.
More than 39% of email fraud across financial services used Gmail.com, Comcast.net, AOL.com, Inbox.lv, or RR.com email addresses.
Part of the defense strategy is simply monitoring the latest scams and ensuring employees are aware of the risks and impact.
Email attacks are a clear and present danger
Proofpoint’s Email Fraud in Financial Services Report key findings also showed:

- Within targeted financial services firms, 56% saw more than five employees targeted by BEC attacks in Q4 2018.
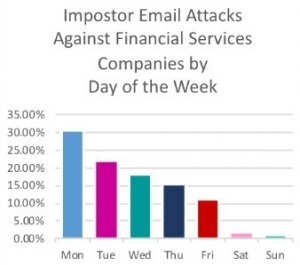
- The largest volume of email fraud attacks targeting financial services companies arrived on weekdays between 7 AM and 2 PM in the target’s time zone, with Mondays being favored by fraudsters.
- In Q4 2018, 39% of email sent from domains owned by financial services companies externally appeared suspicious or were categorized as unverified. That figure includes 68% sent to employees appeared suspicious, 36% sent to customers, and 19% sent to business partners.
Imposter emails are not only targeting companies and their employees but also customers and business partners, which makes security a big challenge.
Businesses need to take a people-centric approach to protect against socially-engineered attacks using strong email defenses and inbound threat blocking capabilities, combined with cybersecurity awareness programs that train users to spot and report malicious emails.
“It is critical that organizations prioritize the implementation of solutions that defend against these attack methods, specifically against domain spoofing, display name spoofing, and look-alike domains, and train employees to identify and report socially-engineered attacks across email, social media, and the web,” Kalember said.
The report is a quick, informative look at imposter email fraud in the financial services industry. You can download Proofpoint’s Email Fraud in Financial Services Report here.
Data visuals courtesy of Proofpoint

